Ransomware Protection Guide: How to Protect Your Practice
Posted by Meditab Software, Inc.
Cyber Security Healthcare Technology Office Management
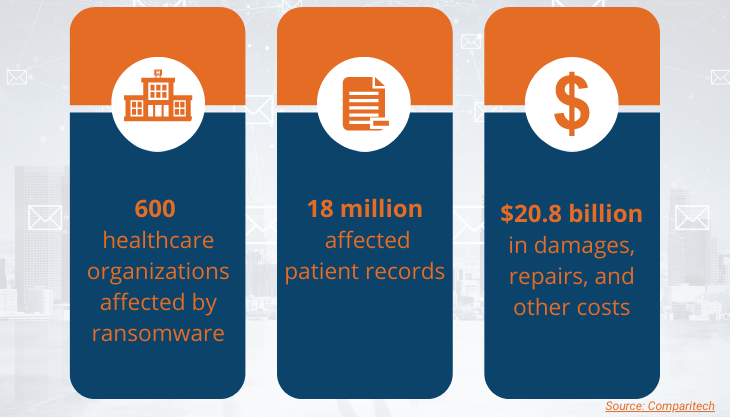
Healthcare has long been the target of ransomware attacks. Healthcare records are more valuable than any bank information due to the amount of personal and financial data in a single record.
The rapid development and adoption of technology in healthcare have created more opportunities for cybercriminals to get a hold of medical information. Meanwhile, COVID-19 and the rise of telehealth and remote work only made it easier for those same criminals to target vulnerabilities in networks, medical devices, and software systems.
The ramifications of ransomware in healthcare go beyond financial damage. It can cripple a practice’s ability to provide care in a timely manner. Plus, legal consequences include HIPAA violation and medical malpractice, adding more burden to your practice, not to mention damaging your reputation and the future of your business.
Read More: Strategies for Supporting the Business Side of Your Practice
The threat of ransomware is serious, so implementing proper prevention measures and having an incident response and recovery plan is crucial to reduce costs, avoid patient care disruption, and decrease the likelihood of data loss.
2020 Statistics on Ransomware Attacks in Healthcare
 What Is Ransomware?
What Is Ransomware?
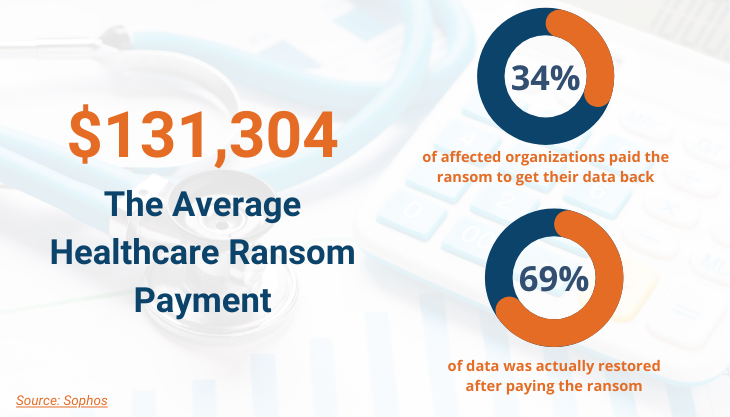
As the name suggests, ransomware is a type of malicious software (malware) that infects your system and encrypts your data. Once affected, you lose access to your data until you pay a “ransom” to buy the decryption key. Healthcare is one of the sectors most likely to pay the ransom, most organizations doing anything to ensure continuity of patient care.
However, even if you pay the ransom, there is no guarantee that the attacker will provide you with the decryption key. Additionally, even if they do, there is no assurance that you will recover 100% of your medical data.
The risk of a ransomware attack in healthcare will always exist because of the profitability of medical data. Attackers can get quick payments from ransoms, sell the patient records, or both.
How Does Ransomware Infect Your System?
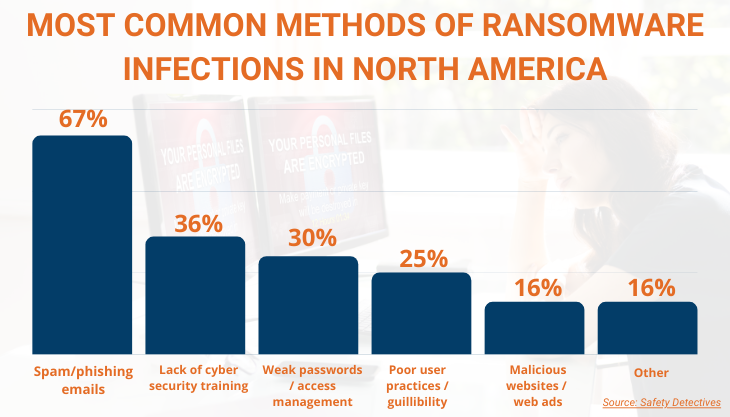
A ransomware virus is commonly disguised as an email attachment or a hyperlink, with the email content typically encouraging you to download the attachment or click the link. Once the user falls for the trick, the malware then silently installs on your device. It can also access your system when you click on an unsafe website or application that contains malicious content.
Once the ransomware has access to your system, it encrypts all of your data files behind a password key held by the attacker.
Ransomware can spread quickly through your system if you're using software that enables you to control computers remotely. More sophisticated ransomware even propagates itself without any human action.
10 Tips for Preventing a Ransomware Attack
There is no single solution to secure your data against a ransomware attack, but you can implement a combination of tools and best practices to prevent a successful attack. The old medical adage that prevention is always better than a cure applies to cybersecurity too.
In healthcare, sometimes the downtime caused by an attack is more detrimental than ransom costs, so having preventive measures in place is essential. Here are ten steps you can follow to prevent a ransomware attack.
1. Educate Your Team
Educating people about the common types of attacks and how it infects your system. Ransomware tactics are evolving and becoming more sophisticated, so it is vital for your team to be aware of these trends and how to avoid them. Provide regular and mandatory security awareness training and conduct simulations to test employee’s knowledge of phishing tactics.
2. Avoid Phishing Emails
Install email spam filters and educate your employees to avoid downloading email attachments from unknown sources. To make sure an email is trustworthy, check the sender and ensure the email address is correct. Verify the email’s legitimacy by contacting the sender directly. Some phishing emails are becoming convincing, even impersonating your company’s CEO.
As remote work took off in 2020, cybercriminals targeted businesses and healthcare workers by sending fake virtual meeting links impersonating their management. The email contained words like “crucial HR meeting” or “lay-off announcements” to draw an emotional reaction and trick the user into clicking past suspicious content.
3. Provide Selective Access
Provide your employees with access to only the systems needed to get their jobs done. IT should revoke access when the user is no longer active.
4. Regularly Update Your Software
To maintain your system’s security, make sure that your software is regularly updated and maintained. Download and install all the latest patches to fix your system’s vulnerabilities. In the absence of a patch, cybercriminals can exploit a vulnerability in your operating system and other software programs and enable them to drop ransomware.
5. Use Strong Passwords and Change Them Often
Set up strong password criteria and inform users not to use the same password across all their accounts. Diversify your passwords so that cybercriminals cannot obtain access to all your accounts at once. Then implement multi-factor authentication to provide an extra layer of security. If a company you’ve recently interacted with was compromised, act fast and change your passwords.
Set passwords to expire after a certain period, and create a locking mechanism that prevents access to the system after several failed login attempts.
6. Closely Monitor Network Traffic
By monitoring your network traffic, you can track unusual activity and identify patterns associated with malware or ransomware. There are several tools available to help administrators with the monitoring and analysis of network traffic.
7. Create a Disaster Recovery Plan
A contingency response plan for ransomware attacks can stop an attack from turning into a full breach and help minimize the impact. It’s also essential to regularly test if your recovery plan works, ensure all your systems are protected, and check that your backups are functional.
8. Limit the Use of Microsoft Office Macros
Many ransomware distributors now use Microsoft Office Macros to deliver their ransomware virus. A macro is a series of commands and instructions that you group as a single command to accomplish a task automatically. Disable macros if they are not required. If your workflow doesn’t allow you to disable them, administrators should block macros like Microsoft Office files (Word, Excel, PowerPoint) downloaded from the Internet.
9. Backup Your Data
Create backup copies of your data regularly and use the 3-2-1 Rule of Data Protection. This rule suggests having three backup copies of your data. Store two of your backup copies in two different systems if the other one fails and store at least one copy offline and offsite. Storing your backup data in an “offsite” location is highly recommended because local “onsite” backups can often become infected as well.
Having both a backup and disaster recovery can go a long way in recovering your data after a ransomware infection and avoiding having to pay the ransom.
Read More: 6 Reasons Why a Cloud-Based EHR System Is Key for Growth
10. Switch to Cloud Hosted Servers
Unlike traditional onsite servers, cloud-hosted servers offer advanced anti-malware protection, daily offsite backups, and automatic software updates. Cloud hosting providers usually include dedicated IT support, firewalls, secure and encrypted solutions, and backups already in their services. With traditional onsite servers, you need to plan and take the essential measures to secure your data yourself.
Traditional onsite servers also run the risk of physical damage during a ransomware attack, causing an additional financial burden when replacing your servers.
Ways to Detect a Ransomware Attack
Early detection is key to preventing a full-blown ransomware attack. The faster you can detect ransomware, the quicker you can react and initiate your disaster response process. Here are four simple ways to detect if ransomware is ongoing.
1. An Increase in File Renaming
When a ransomware attack is currently in progress, there's usually a huge increase in file renaming as data gets encrypted. This is the most reliable method to detect an attack.
An alert can be triggered whenever file renames exceed a pre-set threshold. Setting the threshold to four file renames per second is recommended. You will know that an attack is in progress as soon as the system exceeds that threshold.
2. Unexpected Network Scanners
Cybercriminals often start a ransomware attack using one computer. From there, they’ll start digging into the network of that computer and work through with what they can gain access to. They do this by installing a network scanning tool. Network scanning tools are legitimate tools, but if you suddenly see an unfamiliar network scanner pop-up, check with your IT or the rest of your staff if anyone is using a network scanner. If not, then it’s time to raise the red flag.
3. Trigger Alerts in Sacrificial Network Shares
Ransomware file encryption usually starts with files on the local machine, then moves on to network shares. Most ransomware progresses through each network share in alphabetical order, such as the A: drive, followed by the B: drive, and so on.
Create a sacrificial network share and place fake files with enticing folder names such as “medical records.” Use an early drive letter such as E: or a drive that precedes your actual drive mappings. Then add in trigger alerts once somebody accesses that file on the folder.
By creating a sacrificial network share, you can set up an early warning system and delay the encryption giving you more time to act. This strategy could provide you the valuable minutes you need to shut down client machines before the infection spreads. Just make sure to inform your staff not to access this sacrificial network share.
4. Update Your IDS Systems with Exploit Kit Detection Rules
Many intrusion detection systems (IDS) and firewalls have exploit kit detection features. Exploit kits are hacking toolkits loaded onto websites that search for vulnerabilities in web browsers and plugins. When a user visits a website hosting an exploit kit, any vulnerabilities are identified and leveraged to download ransomware.
Make sure your exploit kit detection tools are updated so they can detect anomalies early on.
Steps You Can Take if Infected with Ransomware
Realizing that your practice has been victim to ransomware can be very stressful, but the first thing to do is remain calm. Giving in to cybercriminals and paying the ransom is rarely the best option. Here are four steps you can take if your data becomes infected by ransomware.
1. Isolate
If you are on any active network, disconnect yourself. This will prevent the virus from spreading and infecting any other device or system. Go offline, disconnect from any wireless capabilities like Bluetooth or WiFi.
2. Investigate and Identify the Scope
Find out exactly how much of your data is compromised and how the attack happened. Knowing exactly how the attack took place can help you close any potential vulnerabilities and strengthen your security.
It is always beneficial to know your enemy, so it is crucial to determine the class of ransomware that has infected your system. Each piece of ransomware has its unique way of infecting your files, and your recovery plan may depend on the type of ransomware. Several sites can help you identify the type of ransomware like ID Ransomware or Crypto Sheriff.
3. Remove the Malware
Clean up the infected computers, devices, data, and files. The best way to ensure that ransomware is completely removed from a system is to wipe out all storage devices and reinstall everything from scratch. Never restore your backup without properly wiping out the malware.
4. Evaluate Your Options For Data Recovery
When you know the type of ransomware you are dealing with, you can initiate your disaster response plan. Here are two options your practice can take to recover your data.
- Restore Data from a Backup
If you have a good backup and disaster recovery plan in place, all you need to do is recover your computer and restore the data. If your backup solution is local and was connected to an infected computer, the chances are that your backup was compromised as well. Offsite backups that were not connected to your network during the time of attack should be good.
- Decrypt Your Files Using an Available Decryptor
In case you didn’t have a backup plan in place or the backup files weren’t good enough, there are various tools that you can use to decrypt your files without having to pay the ransom. Avast and The No More Ransom Project offer such tools for free. However, ransomware is becoming more sophisticated, and some of it can defeat even the best decryption tools.
An Easy Solution to a Continuous Threat
 Ransomware is evolving, and medical data will always be attractive to cybercriminals. The good thing is that you can also increase your cybersecurity awareness and prepare.
Ransomware is evolving, and medical data will always be attractive to cybercriminals. The good thing is that you can also increase your cybersecurity awareness and prepare.
Implementing preventive measures, combined with human monitoring and intervention by skilled professionals, is your best defense against ransomware. Technology can give you the scale and automation you need, but human experts can detect early signs of a ransomware attack and stop it.
Meditab has partnered with ER Tech Pros to provide our clients with cloud hosting and other infrastructure to protect against ransomware, system failures, and a range of costly threats.
ER Tech Pros uses military-grade data encryption, firewalls, and antivirus technologies to prevent an attack before it happens. The team can also help you create a recovery plan and prepare your practice for all the latest threats.
Share this post: on Twitter on Facebook on Google+


